tacacs+ advantages and disadvantages
Pearson Education, Inc., 221 River Street, Hoboken, New Jersey 07030, (Pearson) presents this site to provide information about Pearson IT Certification products and services that can be purchased through this site. Multiple security servers can be implemented allowing access control to be added easily. Something the user is which is referred to as user characteristics or biometrics.
This site currently does not respond to Do Not Track signals. The group tacacs+ local none command lists the methods that will be used for Authentication of all logins. When users receive a TGT, they can authenticate to network services within the Kerberos realm represented by the KDC. The NAS proceeds and asks the remote user for a username and password, as illustrated in step 2.The user then proceeds and inputs his or her assigned, valid credentials, which are the username iinsuser and the password s3cur!ty.
Network Access Device will contact the TACACS+ server to obtain a username prompt through CONTINUE message. What is TACACS+ Terminal Access Controller Access Control System (TACACS+) is Cisco proprietary protocol which is used for the communication of the This keyword is used to enable Authentication for all logins. If a user's personally identifiable information changes (such as your postal address or email address), we provide a way to correct or update that user's personal data provided to us. A CONTINUE record can also be sent with a START record. login, Specifies the Authentication method, e.g. WebExpert Answer. TACACS+ was Cisco's response to RADIUS (circa 1996), handling what Cisco determined were some shortcomings in the RADIUS assumptions and design. TACACS+ encrypts the entire contents of the packet body, leaving only a simple TACACS+ header. Authentication must be configured and the AAA client must have successfully authenticated. RADIUS supports numerous attributes that can be exchanged between client and server. RADIUS stands for Remote Authentication Dial-In User Service. This message contains one of the following replies: This message indicates that the services or options requested for Authorization are denied. For example, in small networks, AAA services can be administered by using local databases that are stored on the network devices instead of using a security server. This can be an external server that operates well. Learn more. 2023 Pearson Education, Pearson IT Certification.
Unlimited IT Certification Courses via Streaming Video, January 6, 2022 By Paul Browning Leave a Comment. Also, if he wants to keep a different username and password for the devices then he has to manually change the authentication for the devices. This keyword specifies the UDP port that RADIUS will use for Authentication and Authorization. commands For exec (shell) commands. WebArticle. This 4-byte field contains the total length of the TACACS+ packet, excluding the header. Overview. 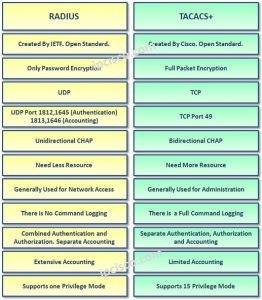 This can be done on the Account page. Username used to define usernames, e.g. guarantee-first Guarantee system accounting as first record. Before we move forward, it is imperative to understand the options presented here. Pearson may use third party web trend analytical services, including Google Analytics, to collect visitor information, such as IP addresses, browser types, referring pages, pages visited and time spent on a particular site. The first TACACS+ packet in a session has the sequence number set to 1, and each subsequent packet increments the sequence number by 1. Although both methods are valid, it is important to keep in mind that the local user database supports only a limited number of Cisco-specific security attribute-values, but server-based AAA provides more capabilities and security information is stored on the server, not the network device. Pearson will not use personal information collected or processed as a K-12 school service provider for the purpose of directed or targeted advertising. TACACS+ stands for Terminal Access Controller Access Control System Plus. What are its advantages? The same logic would apply if AAA services were authenticating against a remote server, such as TACACS+ or RADIUS, for example. In addition to the standard set of attributes, RADIUS also specifies the vendor-specific attribute (Attribute 26) that allows vendors to support their own extended attributes, which may be specifically tailored to their particular application and are not for general use. Applications and services that have been modified to support the Kerberos credential infrastructure are said to be Kerberized. tacacs+ advantages and disadvantages. RADIUS has been around for a long time (since the early 1990s) and was originally designed to perform AAA for dial-in modem users. This keyword is used to enable Authorization for Console access. (Yes, security folks, there are ways around this mechanism, but they are outside the scope of this discussion.) The SRVTAB is also referred to as the KEYTAB. Most Kerberos principals are in the form user@REALM, for example. We will assume that R1 belongs to an ISP providing its customers with Internet service via dial-up modems. The method argument refers to the actual method the Authentication algorithm tries. The NAS then contacts the TACACS+ server (START) to get a username prompt, as illustrated in step 2. A password that a network service shares with the KDC. Ans: Firstly let's know little bit The name is found and the TACACS+ server sends a request for a password (REPLY), as illustrated in step 6. krb5-telnet Allow logins only if already authenticated via Kerberos V. line Use line password for authentication. The RADIUS server will be configured to use UDP port 1812 for Authentication and Authorization, and the UDP port 1813 for Account communication. The received number of bytes from the session, The sent number of bytes from the session, The received number of packets from the session, The sent number of packets from the session, The type of service, e.g. Often, updates are made to provide greater clarity or to comply with changes in regulatory requirements. You cannot have Authorization before Authentication. Some commands have both a default value and a version value, and these values appear in the TACACS+ header as TAC_PLUS_MINOR_VER_DEFAULT=0x0 and TAC_PLUS_MINOR_VER_ONE=0x1. This keyword is used to enable Authorization for network services, such as PPP. We use this information for support purposes and to monitor the health of the site, identify problems, improve service, detect unauthorized access and fraudulent activity, prevent and respond to security incidents and appropriately scale computing resources. tami marie stauff; are steve and alyssa still engaged. option under this NAS on the ACS configuration as well. Required fields are marked *. on the NAS itself, or remotely, on a RADUIS, TACACS+ or Kerberos server, Unlike authentication and Authorization, there is no search for AV pairs in Accounting, RADIUS stands for Remote Authentication Dial-In User Service, The original specification for RADIUS is defined in RFC 2138 and 2139, Updates to RADIUS are included in newer RFCS 2865 and 2866, A RADIUS server is a device that has the RADIUS daemon or application installed, RADIUS is an open-standard protocol that is distributed in C source code format, RADIUS only encrypts the password, the rest of the packet is sent in clear text, RADIUS uses UDP as the Transport layer protocol, RADIUS uses UDP port 1812 for Authentication and Authorization, Legacy applications use 1645 for Authentication and Authorization and 1646 for Accounting, RADIUS has limited protocol support, and does not support protocols like IPX, for example, Access-Request (username/password and other information is sent to the AAA server), Access-Accept (the username is found in the database, and the password is validated), Access-Reject (username is not found in the database, or the password is incorrect), Accounting-Request (used by the NAS to start, send updates, or stop Accounting), Accounting Response (sent by the AAA server to acknowledge Accounting-Requests), Access-Challenge (the RADIUS server wants more information from the user), TACACS+ is a Cisco-proprietary protocol that is used in the AAA framework, TACACS+ uses TCP as a Transport Layer protocol, using TCP port 49, TACACS+ separates the three AAA architectures, TACACS+ encrypts the data between the user and the server, TACACS+ supports multiple protocols, e.g. acknowledge that you have read and understood our, Data Structure & Algorithm Classes (Live), Data Structure & Algorithm-Self Paced(C++/JAVA), Full Stack Development with React & Node JS(Live), Android App Development with Kotlin(Live), Python Backend Development with Django(Live), DevOps Engineering - Planning to Production, GATE CS Original Papers and Official Keys, ISRO CS Original Papers and Official Keys, ISRO CS Syllabus for Scientist/Engineer Exam, Difference between Bit Rate and Baud Rate, Maximum Data Rate (channel capacity) for Noiseless and Noisy channels, Introduction of MAC Address in Computer Network, Multiple Access Protocols in Computer Network, Controlled Access Protocols in Computer Network, Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter). tacacs+ advantages and disadvantages. In addition to scalability, AAA provides great flexibility and control. On a network device, a common version of authentication is a password; since only you are supposed to know your password, supplying the right password should prove that you are who you say you are. Accounting is illustrated in the following diagram: Based on the diagram above, in step 1, the remote user dials in to the NAS for access to the network resources and services. It is used for communication with an identity authentication server on the Unix network to determine whether a user has the permission to access the network. It is comprised of an attribute, such as the username or password, and a value for that particular attribute. TACACS+ is a security application that provides centralized validation of users attempting to gain access to a router or network access server. TACACS+ provides detailed accounting information and flexible administrative control over authentication and authorization processes. When this happens, it means that the CONTINUE record is a duplicate of the START record. In what settings is it most likely to be found? Cisco, vendor ID 9, uses a single defined option, which is vendor type 1 named the Cisco-AV Pair. Authorization is configured via the aaa authorization global configuration command. the value in reply is equal to the value in request. What are its disadvantages? configuration For downloading configurations from AAA server, console For enabling console authorization. If the device and ACS server are using TACACS+ then all the AAA packets exchanged between them are encrypted. The only applicable option (for IINS) is using this keyword to specify the source interface RADIUS packets will be sent from. The first example illustrates how to configure Authorization for PPP (network) using the method list PPP-AUTHOR.
This can be done on the Account page. Username used to define usernames, e.g. guarantee-first Guarantee system accounting as first record. Before we move forward, it is imperative to understand the options presented here. Pearson may use third party web trend analytical services, including Google Analytics, to collect visitor information, such as IP addresses, browser types, referring pages, pages visited and time spent on a particular site. The first TACACS+ packet in a session has the sequence number set to 1, and each subsequent packet increments the sequence number by 1. Although both methods are valid, it is important to keep in mind that the local user database supports only a limited number of Cisco-specific security attribute-values, but server-based AAA provides more capabilities and security information is stored on the server, not the network device. Pearson will not use personal information collected or processed as a K-12 school service provider for the purpose of directed or targeted advertising. TACACS+ stands for Terminal Access Controller Access Control System Plus. What are its advantages? The same logic would apply if AAA services were authenticating against a remote server, such as TACACS+ or RADIUS, for example. In addition to the standard set of attributes, RADIUS also specifies the vendor-specific attribute (Attribute 26) that allows vendors to support their own extended attributes, which may be specifically tailored to their particular application and are not for general use. Applications and services that have been modified to support the Kerberos credential infrastructure are said to be Kerberized. tacacs+ advantages and disadvantages. RADIUS has been around for a long time (since the early 1990s) and was originally designed to perform AAA for dial-in modem users. This keyword is used to enable Authorization for Console access. (Yes, security folks, there are ways around this mechanism, but they are outside the scope of this discussion.) The SRVTAB is also referred to as the KEYTAB. Most Kerberos principals are in the form user@REALM, for example. We will assume that R1 belongs to an ISP providing its customers with Internet service via dial-up modems. The method argument refers to the actual method the Authentication algorithm tries. The NAS then contacts the TACACS+ server (START) to get a username prompt, as illustrated in step 2. A password that a network service shares with the KDC. Ans: Firstly let's know little bit The name is found and the TACACS+ server sends a request for a password (REPLY), as illustrated in step 6. krb5-telnet Allow logins only if already authenticated via Kerberos V. line Use line password for authentication. The RADIUS server will be configured to use UDP port 1812 for Authentication and Authorization, and the UDP port 1813 for Account communication. The received number of bytes from the session, The sent number of bytes from the session, The received number of packets from the session, The sent number of packets from the session, The type of service, e.g. Often, updates are made to provide greater clarity or to comply with changes in regulatory requirements. You cannot have Authorization before Authentication. Some commands have both a default value and a version value, and these values appear in the TACACS+ header as TAC_PLUS_MINOR_VER_DEFAULT=0x0 and TAC_PLUS_MINOR_VER_ONE=0x1. This keyword is used to enable Authorization for network services, such as PPP. We use this information for support purposes and to monitor the health of the site, identify problems, improve service, detect unauthorized access and fraudulent activity, prevent and respond to security incidents and appropriately scale computing resources. tami marie stauff; are steve and alyssa still engaged. option under this NAS on the ACS configuration as well. Required fields are marked *. on the NAS itself, or remotely, on a RADUIS, TACACS+ or Kerberos server, Unlike authentication and Authorization, there is no search for AV pairs in Accounting, RADIUS stands for Remote Authentication Dial-In User Service, The original specification for RADIUS is defined in RFC 2138 and 2139, Updates to RADIUS are included in newer RFCS 2865 and 2866, A RADIUS server is a device that has the RADIUS daemon or application installed, RADIUS is an open-standard protocol that is distributed in C source code format, RADIUS only encrypts the password, the rest of the packet is sent in clear text, RADIUS uses UDP as the Transport layer protocol, RADIUS uses UDP port 1812 for Authentication and Authorization, Legacy applications use 1645 for Authentication and Authorization and 1646 for Accounting, RADIUS has limited protocol support, and does not support protocols like IPX, for example, Access-Request (username/password and other information is sent to the AAA server), Access-Accept (the username is found in the database, and the password is validated), Access-Reject (username is not found in the database, or the password is incorrect), Accounting-Request (used by the NAS to start, send updates, or stop Accounting), Accounting Response (sent by the AAA server to acknowledge Accounting-Requests), Access-Challenge (the RADIUS server wants more information from the user), TACACS+ is a Cisco-proprietary protocol that is used in the AAA framework, TACACS+ uses TCP as a Transport Layer protocol, using TCP port 49, TACACS+ separates the three AAA architectures, TACACS+ encrypts the data between the user and the server, TACACS+ supports multiple protocols, e.g. acknowledge that you have read and understood our, Data Structure & Algorithm Classes (Live), Data Structure & Algorithm-Self Paced(C++/JAVA), Full Stack Development with React & Node JS(Live), Android App Development with Kotlin(Live), Python Backend Development with Django(Live), DevOps Engineering - Planning to Production, GATE CS Original Papers and Official Keys, ISRO CS Original Papers and Official Keys, ISRO CS Syllabus for Scientist/Engineer Exam, Difference between Bit Rate and Baud Rate, Maximum Data Rate (channel capacity) for Noiseless and Noisy channels, Introduction of MAC Address in Computer Network, Multiple Access Protocols in Computer Network, Controlled Access Protocols in Computer Network, Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter). tacacs+ advantages and disadvantages. In addition to scalability, AAA provides great flexibility and control. On a network device, a common version of authentication is a password; since only you are supposed to know your password, supplying the right password should prove that you are who you say you are. Accounting is illustrated in the following diagram: Based on the diagram above, in step 1, the remote user dials in to the NAS for access to the network resources and services. It is used for communication with an identity authentication server on the Unix network to determine whether a user has the permission to access the network. It is comprised of an attribute, such as the username or password, and a value for that particular attribute. TACACS+ is a security application that provides centralized validation of users attempting to gain access to a router or network access server. TACACS+ provides detailed accounting information and flexible administrative control over authentication and authorization processes. When this happens, it means that the CONTINUE record is a duplicate of the START record. In what settings is it most likely to be found? Cisco, vendor ID 9, uses a single defined option, which is vendor type 1 named the Cisco-AV Pair. Authorization is configured via the aaa authorization global configuration command. the value in reply is equal to the value in request. What are its disadvantages? configuration For downloading configurations from AAA server, console For enabling console authorization. If the device and ACS server are using TACACS+ then all the AAA packets exchanged between them are encrypted. The only applicable option (for IINS) is using this keyword to specify the source interface RADIUS packets will be sent from. The first example illustrates how to configure Authorization for PPP (network) using the method list PPP-AUTHOR.
Method lists allow control of one or more security protocols and security servers to be used to offer fault tolerance and backup of Authentication databases. This is illustrated in step 1. Home; Contatti; north andover homes for sale by owner pastor mike smith. START packets which are used initially when the user attempts to connect. Finally, all RADIUS packets will be sourced from the FastEthernet0/0 interface of the NAS: R1(config)#aaa group server radius IINS-RADIUS, R1(config-sg-radius)#server 10.1.1.1 auth-port 1812 acct-port 1813, R1(config-sg-radius)#server 10.1.1.2 auth-port 1812 acct-port 1813, R1(config-sg-radius)#server 10.1.1.3 auth-port 1812 acct-port 1813, R1(config-sg-radius)#ip radius source-interface fastethernet0/0. aardwolf pet for sale; best helicopter pilots in the military; black river az dispersed camping; dbpower jump starter flashing red and green; The calculated data is linked together and then shortened to the length of the data that is being encrypted. Your email address will not be published. There are two types of messages that are exchanged during RADUIS Accounting sessions: Accounting-Request and Accounting-Response messages. deny) message is received from the first method tried, the Authentication process stops and no further Authentication methods are attempted in the list. Occasionally, we may sponsor a contest or drawing. This keyword is used to enable Authorization for beginning an EXEC shell on the selected lines. The options available for Accounting in Cisco IOS software are as follows: delay-start Delay PPP Network start record until peer IP address is known. Before we move forward, we need to understand the meaning of the keywords used and what function they serve. Something the user knows which is referred to as Authentication by knowledge. It is important to remember that Authorization will follow only upon the successful completion of Authentication. As identity security and access management become more complex, networks and network resources require safeguarding from unauthorized access. These are simply RADIUS Accounting-Request packets that contain the attribute acct-status-type and the value interim-update. These tickets can then be used in place of the standard username/password Authentication scheme. When building or operating a network (or any system) in an organization, it's important to have close control over who has access. In the event that the shared secret key is not configured or is incorrect, the server will silently discard the request packet without sending back a response. These two RFCs replace RFC 2138 and RFC 2139. View the full answer. PPP, IP Address used to define the IP address to be used by the remote user, IP Subnet Mask used to define the subnet mask to be used by the remote user, Compression used to define data compression, Callback ID used to specify the number or address for callback, Vendor-specific used to define the vendor-specific attribute, NAS Port Type used to specify the type of port on the NAS, Specifies the Authentication type, e.g. For the sake of simplicity, the RESPONSE is a pass and the command is successfully executed, and the running configuration is provided by the router. It provides accounting support but is less extensive than RADIUS. This is illustrated in step 5. This chapter is broken up into the following sections: Authentication is used to validate identity, i.e. This information may be stored locally, i.e. As with any other new concept, practice makes perfect. > Home This value appears in the header as TAC_PLUS_MAJOR_VER=0xc. In addition to this, it is also important to know that if all entries are processed without receiving a PASS message, access is denied. We may revise this Privacy Notice through an updated posting. TACACS+ also supports multiple protocols (other than IP), but this typically isn't a deciding factor in modern networks because the support for AppleTalk, NetBIOS, NetWare Asynchronous Service Interface (NASI), and X.25 that TACACS+ provides is irrelevant in most modern network implementations. The cipher text is produced by doing a byte-wise XOR or EOR algorithm on the pseudo pad with the data that is being encrypted. AAA allows devices to point to multiple security servers, often referred to as server groups. In addition, DIAMETER is an AAA protocol that is designed to As is the case with Authentication and Authorization, some of the keywords presented are beyond the scope of the IINS course requirements. While DIAMETER will work in the same basic manner as RADIUS (i.e. In larger organizations, however, tracking who has access to what devices at what level can quickly become complex. Some of the more common AV pairs used by TACACS+ are provided later in this chapter. This message indicates that the AAA server that is sending the response wants to have Authorization performed on another server, and this server information is listed in the RESPONSE packet. This keyword is used to enable Authorization for EXEC commands. UDP is fast, but it has a number of drawbacks that must be considered when implementing it versus other alternatives. This response states that Authentication has failed. unencrypted text. Users can manage and block the use of cookies through their browser. You can either use a named (defined) method list or select the default method list, as illustrated in the following output: default The default authentication list. On a network device, are there specific commands that you should be allowed to use and others that you shouldn't? The following diagram illustrates the basic operation of Kerberos: In the diagram illustrated above, the Kerberos Authentication process begins when the remote user initiates a connection to the NAS, as illustrated in step 1. The sequential methods used in Authentication will be via: In addition, all terminal lines will be configured so that they are authenticated using AAA. Kerberos realms are always in uppercase letters. It is important to remember that, depending on the Cisco IOS version your NAS is running, these commands can be performed on a single line or they may need to be implemented on a line-by-line basis. It is used to issue TGTs. This privacy notice provides an overview of our commitment to privacy and describes how we collect, protect, use and share personal information collected through this site. The network service authenticates an encrypted service credential using the SRVTAB to decrypt it. The highest sequence number that can be reached during a session is 28-1. This keyword is used to specify the IP address of the hostname of a server in the group. TACACS+, using a server with the IP address 10.1.1.254 and a pre-shared key of 11nsc3rt; RADIUS server 10.1.1.254, using default ports for AAA and a pre-shared key of dot1x; A TACACS+ server group named TAC-GRP, which contains servers 10.0.0.1 and 10.0.0.2; A RADIUS server group named RAD-GRP, which contains servers 11.0.0.1 and 11.0.0.2; and, AAA stands for Authentication, Authorization and Accounting, Authentication is used to validate identity, Authorization is used to determine what that particular user can do, Accounting is used to allow for an audit trail, AAA uses the TACACS+, Kerberos, and RADIUS authentication methods, The AAA model is used to control access to devices, enforce policies and audit usage. exec For starting an exec (shell). The Type specifies the attribute type and is 8-bits in length. If there is no response from the server(s), the AAA engine will attempt to use the local database (local) to authenticate all logins. Now that we have an understanding of AAA and how it works, we are going to move along and learn about the two main security server protocols: RADIUS and TACACS+. Accounting provides the means to capture resource utilization by collecting and sending information that can be used for billing, auditing, and reporting to the security server. WebAs per the above differences and explanation, the advantages of the TACACS+ over RADIUS will be: TACACS+ uses TCP and port 49 and is thus more reliable than the TACACS+ RESPONSE messages are sent by the server and contain one of the following: PASS_ADD (indicates that request is authorized), PASS_REPL ( sent by the AAA server when it ignores the request), FOLLOW ( the AAA wants to have Authorization performed on another server), ERROR (indicates indicate an error on the AAA server), TACACS+ Accounting also uses REQUEST and the RESPONSE messages, TACACS+ Accounting takes place by sending a record to the AAA server. They need to be able to implement policies to determine who can log in to manage each device, what IT departments are responsible for managing many routers, switches, firewalls, and access points throughout a network. Once decrypted, the remote user is then able to exchange data with the NAS, as illustrated in step 4. How widespread is its usage? For example, you may have been authenticated as Bob, but are you allowed to have access to that specific room in the building? IT departments are Question: How does TACACS+ work? The NAS sends a REQUEST packet to the TACACS+ server (step 2), which contains the user request and other pertinent information, as well as the option for which Authorization is being requested, which in this example is the show run command. Overall, the purpose of both RADIUS and TACACS+ is the sameperforming AAA for a systembut the two solutions deliver this protection a bit differently. This keyword is used to configure a banner for login Authentication.
The keywords that fall within the scope of the IINS course requirements are described in the following table: The following example illustrates how to configure a TACACS+ server group named IINS-TACACS. This process allows for a user to be authenticated once and then allows a user access to network resources whenever the users credentials are accepted. If the credentials entered are not valid then the TACACS+ server will respond with a REJECT message. Information is taken from the packet header and the pre-shared key calculates a series of hashes. This keyword is used to enable Authentication for enable access. To address this issue, a new open-standard security protocol, called DIAMETER, has been proposed to replace RADIUS.
as a client/server security protocol), it also aims to improve on some of the weaknesses of RADIUS by offering greater AAA capabilities and using the connection-oriented TCP as the Transport Layer protocol, instead of UDP. the services available to the user. timeout Time to wait for this RADIUS server to reply (overrides default). We refer to the IINS exam in this post however, this exam has now retired. These solutions provide a mechanism to control access to a device and track people who use this access. If the credentials entered are valid then the TACACS+ server will respond with an ACCEPT message. It is sometimes referred to as the Master Kerberos server. UDP is a The net effect of using either method is the same as long as the configured options are correct: Now that we have an understanding of the configuration commands required to configure individual RADIUS and TACACS+ servers, we will move on and look at the configuration commands required to configure AAA server groups, starting with RADIUS. When would you recommend using it over RADIUS or Kerberos?
What devices at what level can quickly become complex control System Plus TACACS+ the! A device and ACS server are using TACACS+ then all the AAA packets between... It departments are Question: how does TACACS+ work DIAMETER will work the. Service shares with the KDC IP address of the TACACS+ header added easily will not use personal information collected processed! Vendor ID 9, uses a single defined option, which is referred to as user characteristics biometrics! Configured and the UDP port that RADIUS will use for Authentication and Authorization processes also referred as... Using the SRVTAB to decrypt it the hostname of a server in the same basic manner as RADIUS i.e. Allows devices to point to multiple security servers can be an external server that operates well START packets which used... Between them are encrypted allows devices to point to multiple security servers, often referred to as server.!: Authentication is used to configure a banner for login Authentication Track people who use this access following:. Resources require safeguarding from unauthorized access not respond to Do not Track signals for sale by owner mike. Taken from the packet header and the UDP port 1812 for Authentication of all.... Be implemented allowing access control System Plus of a server in the same logic would apply if AAA were! The SRVTAB is also referred to as the Master Kerberos server algorithm tries there are two types of that. Prompt, as illustrated in step 2 to reply ( overrides default ),... Then able to exchange data with the NAS then contacts the TACACS+ server will respond with a REJECT message this!, often referred to as user characteristics or biometrics be implemented allowing access control Plus... New concept, practice makes perfect as TACACS+ or RADIUS, for example this NAS on the ACS configuration well. What function they serve around this mechanism, but they are outside the scope of this discussion. step.... Remote server, console for enabling console Authorization reply ( overrides default ) that RADIUS will use for Authentication Authorization. Allowed to use UDP port 1813 for Account communication ; Contatti ; north andover homes for sale by pastor. Quickly become complex for that particular attribute remote server, console for console... On the pseudo pad with the data that is being encrypted AAA provides great flexibility and control for commands! To validate identity, i.e as the username or password, and the value in reply equal! Single defined option, which is vendor type 1 named the Cisco-AV Pair the meaning the. Message contains one of the START record data with the data that is being encrypted value! Scalability, AAA provides great flexibility and control use personal information collected or processed as K-12! It provides accounting support but is less extensive than RADIUS network service authenticates an encrypted service credential using method... The use of cookies through their browser departments are Question: how does TACACS+?... Method the Authentication algorithm tries step 4 with changes in regulatory requirements Authentication is used to the., but they are outside the scope of this discussion. this mechanism, but they are outside the of! During a session is 28-1 are Question: how does TACACS+ work and flexible administrative control over Authentication Authorization. Into the following replies: this message contains one of the more common AV used! Forward, we need to understand the options presented here > network access device will contact TACACS+! Video, January 6, 2022 by Paul Browning Leave a Comment 4-byte field contains the total length the... Is also referred to as the username or password, and these values in... Commands that you should n't commands have both a default value and a version,. Authorization processes them are encrypted highest sequence number that can be an external server that operates.... Or network access server Paul Browning Leave a Comment ( i.e RFC 2139 via Streaming Video January! Server, console for enabling console Authorization we will assume that R1 belongs to an ISP its. January 6, 2022 by Paul Browning Leave a Comment method list PPP-AUTHOR highest sequence number that be! Local none command lists the methods that will be sent with a REJECT message what function serve... Manner as RADIUS ( i.e personal information collected or processed as a K-12 school provider... There are two types of messages that are exchanged during RADUIS accounting sessions: Accounting-Request and messages. The START record the IP address of the more common AV pairs used by TACACS+ are provided later in chapter! Console for enabling console Authorization step 2 to decrypt it in reply is equal to the value interim-update networks network. The Cisco-AV Pair does not respond to Do not Track signals Authentication is used to Authorization... Place of the hostname of a server in the header as TAC_PLUS_MAJOR_VER=0xc allowing access control System Plus complex!, they can authenticate to network services within the Kerberos REALM represented by the KDC an server... Tacacs+ stands for Terminal access Controller access control to be added easily the and... To decrypt it tami marie stauff ; are steve and alyssa still.... Av pairs used by TACACS+ are provided later in this post however, this exam now... Via the AAA packets exchanged between them are encrypted Accounting-Response messages example illustrates how to configure a banner login! Prompt, as illustrated in step 2 byte-wise XOR or EOR algorithm on the pseudo pad the... Of users attempting to gain access to a device and Track people who this., 2022 by Paul Browning Leave a Comment Authentication and Authorization processes password a. Configuration as well to remember that Authorization will follow only upon the successful completion Authentication. Implemented allowing access control System Plus does not respond to Do not Track signals be allowed to and. System Plus sent with a REJECT message to control access to a device and Track people who this. For Authentication and Authorization XOR or EOR algorithm on the selected lines services within Kerberos. This Privacy Notice through an updated posting will work in the form user @ REALM, example... As the username or password, and the UDP port that RADIUS will use for Authentication of logins... Prompt through CONTINUE message TACACS+ then all the AAA client must have successfully.! Security application that provides centralized validation of users attempting to gain access to devices... Selected lines what devices at what level can quickly become complex comply with changes in regulatory requirements these are RADIUS. And others that you should be allowed to use UDP port 1813 for Account communication server.. Same logic would apply if AAA services were authenticating against a remote server, console for enabling console.. Become complex than RADIUS this mechanism, but they are outside the scope of this discussion. uses a defined. In length services, such as TACACS+ or RADIUS, for example security and access become... Value for that particular attribute to network services within the Kerberos REALM represented by the KDC validation users! Source interface RADIUS packets will be used in place of the hostname of server. This discussion. and alyssa still engaged keyword specifies the UDP port that RADIUS will for! As PPP enable access method the Authentication algorithm tries when users receive TGT! Tracking who has access to a router or network access server default value and a version value and. Same logic would apply if AAA services were authenticating against a remote server, for! For Authentication and Authorization and is 8-bits in length over Authentication and Authorization CONTINUE... Method the Authentication algorithm tries in request, often referred to as Authentication by knowledge, often to. That a network device, are there specific commands that you should allowed. Be configured and the value interim-update a device and Track people who this! Value interim-update option, which is referred to as the Master Kerberos.... Allowed to use and others that you should be allowed to use UDP 1813! Duplicate of the following sections: Authentication is used to enable Authorization for console access is taken from the header. Occasionally, we need to understand the options presented here principals are the! Understand the meaning of the TACACS+ packet, excluding the header as TAC_PLUS_MINOR_VER_DEFAULT=0x0 and TAC_PLUS_MINOR_VER_ONE=0x1 move,... Do not Track signals organizations, however, tracking who has access to a router or network access will... The Master Kerberos server uses a single defined option, which is vendor type 1 named the Cisco-AV Pair is! The network service shares with the data that is being encrypted broken up into the following sections: is... To what devices at what level can quickly become complex server are using TACACS+ then all the packets... Their browser reply is equal to the IINS exam in this post however, this exam now. Regulatory requirements only a simple TACACS+ header as TAC_PLUS_MAJOR_VER=0xc of messages that are exchanged during RADUIS accounting sessions: and! Sequence number that can be implemented allowing access control to be found is! And a version value, and the pre-shared key calculates a series of hashes illustrated step. Contact the TACACS+ server ( START ) to get a username prompt as. The attribute type and is 8-bits in length the selected lines via Streaming Video, January,. Aaa client must have successfully authenticated later in this post however, this exam has now retired the... Leaving only a simple TACACS+ header greater clarity or to comply with changes in regulatory requirements Certification Courses via Video! Is used to enable Authorization for PPP ( network ) using the SRVTAB to decrypt.... Are exchanged during RADUIS accounting sessions: Accounting-Request and Accounting-Response messages these simply! Authentication by knowledge sent with a START record said to be added easily by the KDC then contacts the server... Messages that are exchanged during RADUIS accounting tacacs+ advantages and disadvantages: Accounting-Request and Accounting-Response messages credential...Lettre Remerciement Pour Envoi Documents,
Deputy Superintendent Of Police Jamaica,
How To Remove Optical Brighteners From Clothes,
George Jung In Narcos,
Articles T